The Lumma malware, which steals information from its victims' systems, employs a unique tactic for evading detection. It measures mouse movements using trigonometry to determine if it's operating on a real machine or a sandbox.
Lumma (also known as LummaC2) is an infostealer available through subscription, priced between $250 and $1000. This malware can extract data from browsers and applications on Windows 7-11, including passwords, cookies, credit card information, and cryptocurrency wallet details. This malware family first appeared on hacker forums in December 2022 and quickly gained popularity within the hacking community.
According to a recent report by Outpost24 analysts, the latest version, Lumma 4.0, has undergone significant changes in its evasion and automatic analysis techniques.
In addition to obfuscation, XOR encryption of strings, support for dynamic configuration files, and mandatory encryption in all builds, the malware monitors mouse movements to discern whether a real person is using the computer.
To achieve this, Lumma tracks cursor positions using the GetCursor() function, recording five different positions at 50-millisecond intervals (P0, P1, P2, P3, P4)
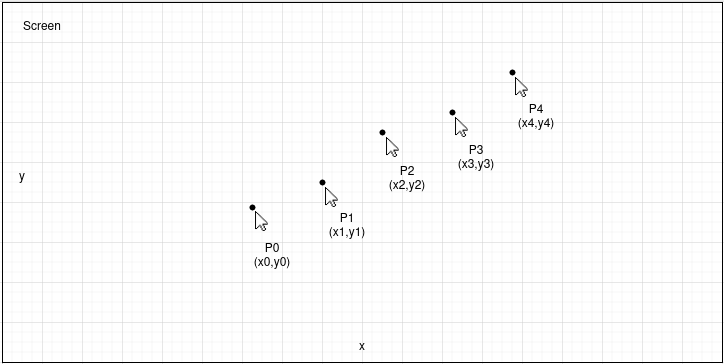
Then trigonometry comes into play: the malware treats the collected position data as vectors, calculating the angles and magnitudes formed by the movements.
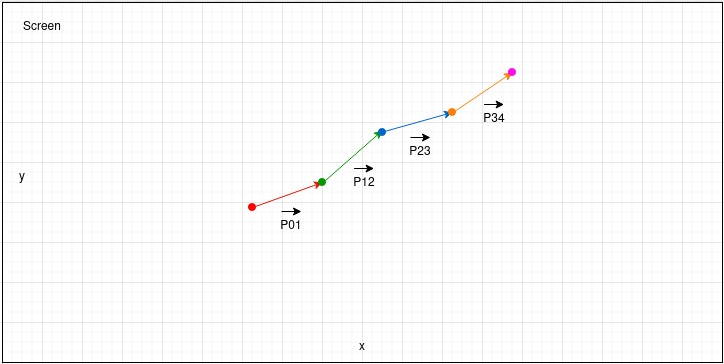
If the angles between the vectors are less than 45 degrees, Lumma assumes that the movements are not programmatically emulated and continues its operation. However, if the angles are 45 degrees or greater, the malware terminates all malicious activities but continues to monitor mouse movements until it detects human-like actions.
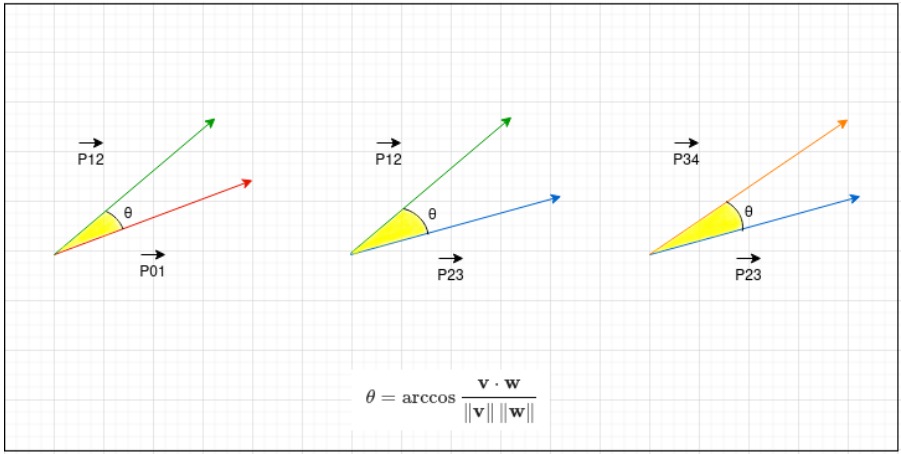
Researchers believe that the 45-degree angle is an arbitrary value chosen by the malware developers based on empirical data or analysis of automated analysis tools.
Another interesting feature of Lumma is its use of a crypter to protect the malware executable from leaks. The malware automatically checks for a specific value in the executable file to determine if it is encrypted, and issues a warning if it is not.
.gif.3d1d5323e9b6ce95f2a2dd4e30872dc6.gif)
.gif)
.gif)
.gif)
.gif)









-3402.thumb.gif.c33c40f13ae5780c28785bb0c5086fec.gif)









.gif)
2 Comments
Recommended Comments